Some other of my technical work.

Demonstrating Web Vulnerabilities
This project explores how vulnerabilities arise in web applications due to design oversights and misconfigurations (which are intentionally baked into the source code). After, these vulnerabilities are discovered through the use of static and dynamic analysis tools, namely SonarQube and OWASP ZAP, respectively. Finally, defensive and prevention mechanisms are put in place in to prevent the vulnerabilities. A simple web application (HTML + Js) was used.
View this project on GitHub↗
SSL Certificate Validity Predictor
This project uses Machine Learning to predict SSL certificate validity based on extracted features, such as the issuer, chosen public key algorithm and size, chosen signature algorithm, and associated domains (SAN). The certificates were gathered via simple connections to a large list of random websites using Python. The RandomForest classifier was trained and evaluated, achieving an accuracy score of 0.978.
View this project on GitHub↗

Pythonic Ping Application
A custom program in Python is developed to implement the ping operation without using any direct pinging functions. The project's barebones nature mainly stems from the design and combination of different checksums.
View this project on GitHub↗
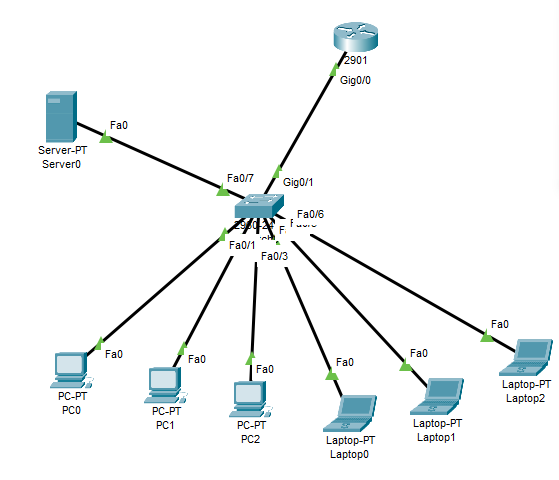
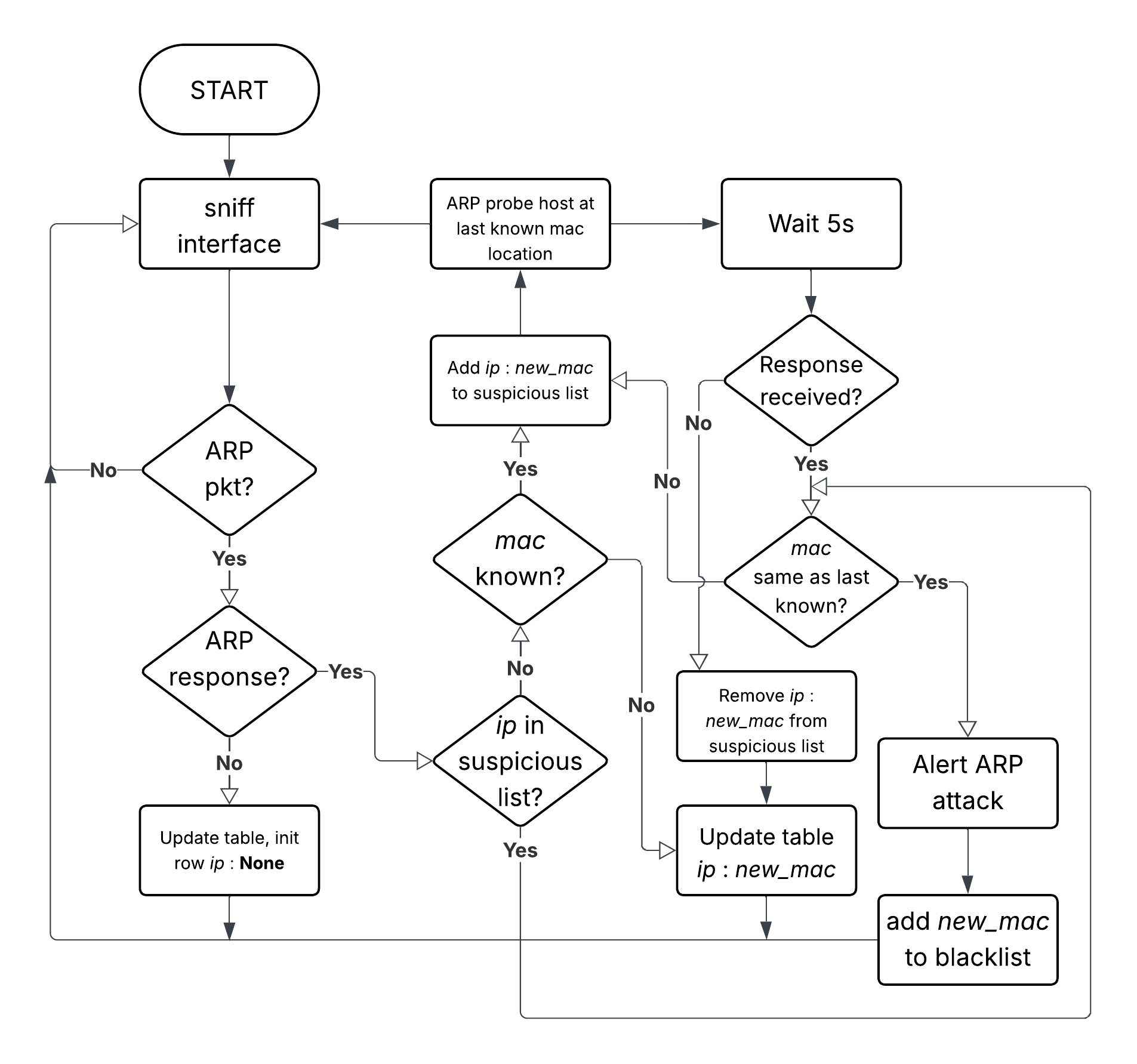
ARP Poisoning Detector
A simple Pythonic scripts listens for ARP requests and responses, updating an internal table accordingly. When a new MAC entry is detected for an already-known device, the detection mechanism sends an ARP request to that device based on its last known IP address. If, after some time, the received ARP response contains the last known MAC address, then the previously received ARP response must have been spoofed.
View this project on GitHub↗
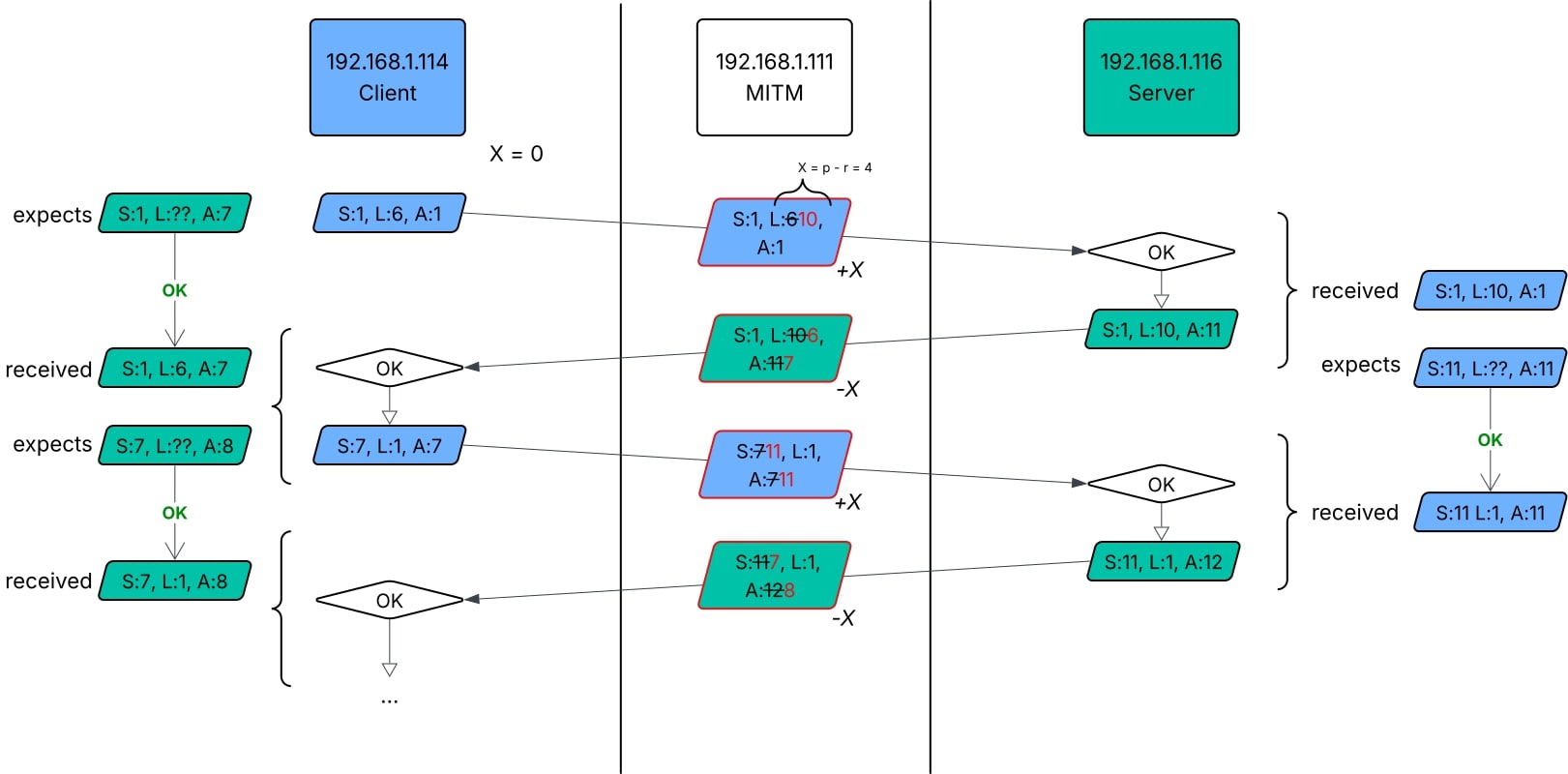
Simple TELNET Hijacker
This attack first involves an ARP jam, wherein the man-in-the-middle (MITM) machine sends its own MAC address as the destination MAC to the target client and server machines. The machine is configured to forward received packets meant for another MAC address (i.e., peer-to-peer). Next, a script sniffs the traffic, then modifies and injects its own payload into the packets. The SEQ and ACK values are processed in a way that the target client and server machines expects of a normal TELNET session; i.e., neither realizes that there was a MITM between them all this time.
View this project on GitHub↗
