A collection of some technical security work I am really happy with
Technical Skills
Languages
Tools, Frameworks, & Libraries
SDN ( Mininet↗, ONOS↗ ), Virtualization & Containerization( VirtualBox↗, VMware↗, Docker↗ ), OS ( Kali Linux↗, Ubuntu↗, Windows↗ ), Forensics ( Autopsy↗, Wireshark↗, Volatility↗ ), Monitoring & Analytics ( Suricata↗, Splunk↗, Microsoft Sentinel↗, Neo4j↗ ), Ethical Hacking ( Nmap↗, Burp Suite↗, Metasploit↗, Tenable Nessus↗, SonarQube↗ ), Malware Analysis ( CFF Explorer↗, Ghidra↗, APIMiner↗, Procwatch↗ ), Cloud ( GCP↗, AWS↗ ), Machine Learning ( sklearn↗, PyTorch↗ ), Computer Vision ( OpenCV↗, librosa↗ ), DevOps ( git↗, VS Code↗, Anaconda Suite↗, Jenkins↗, Android Studio↗, MS Power Automate↗ ), Academic ( LaTeX↗, Overleaf↗, Neptune↗ )
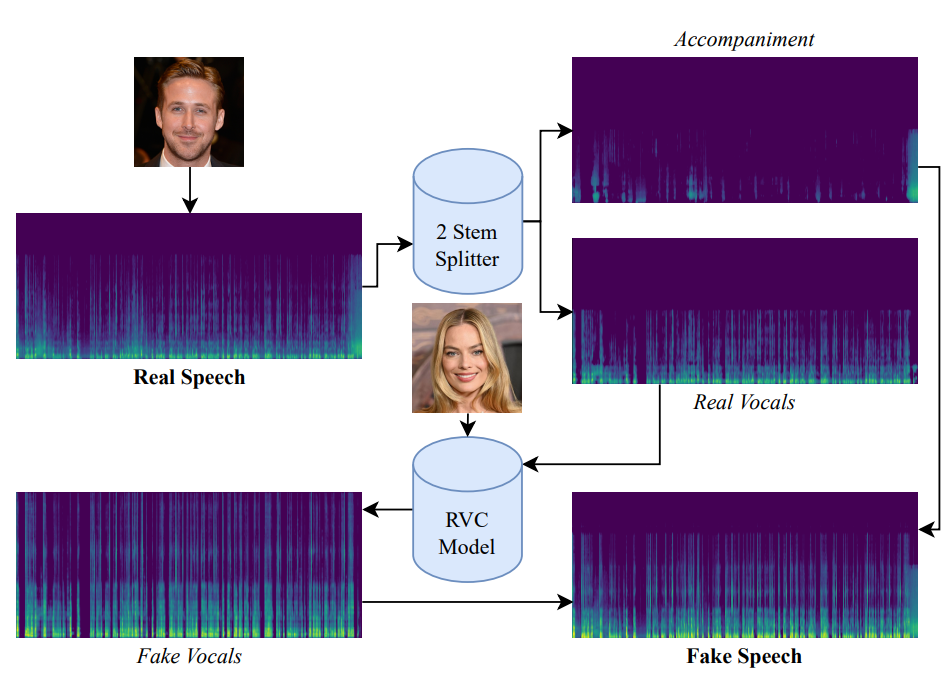
Real-time Detection of RVC-based DeepFaked Audio
Audio impersonation has become more accessible due to the rising popularity of machine and deep learning. This project explores how machine learning can also be used to detect them in real-time.
View this project on GitHub↗
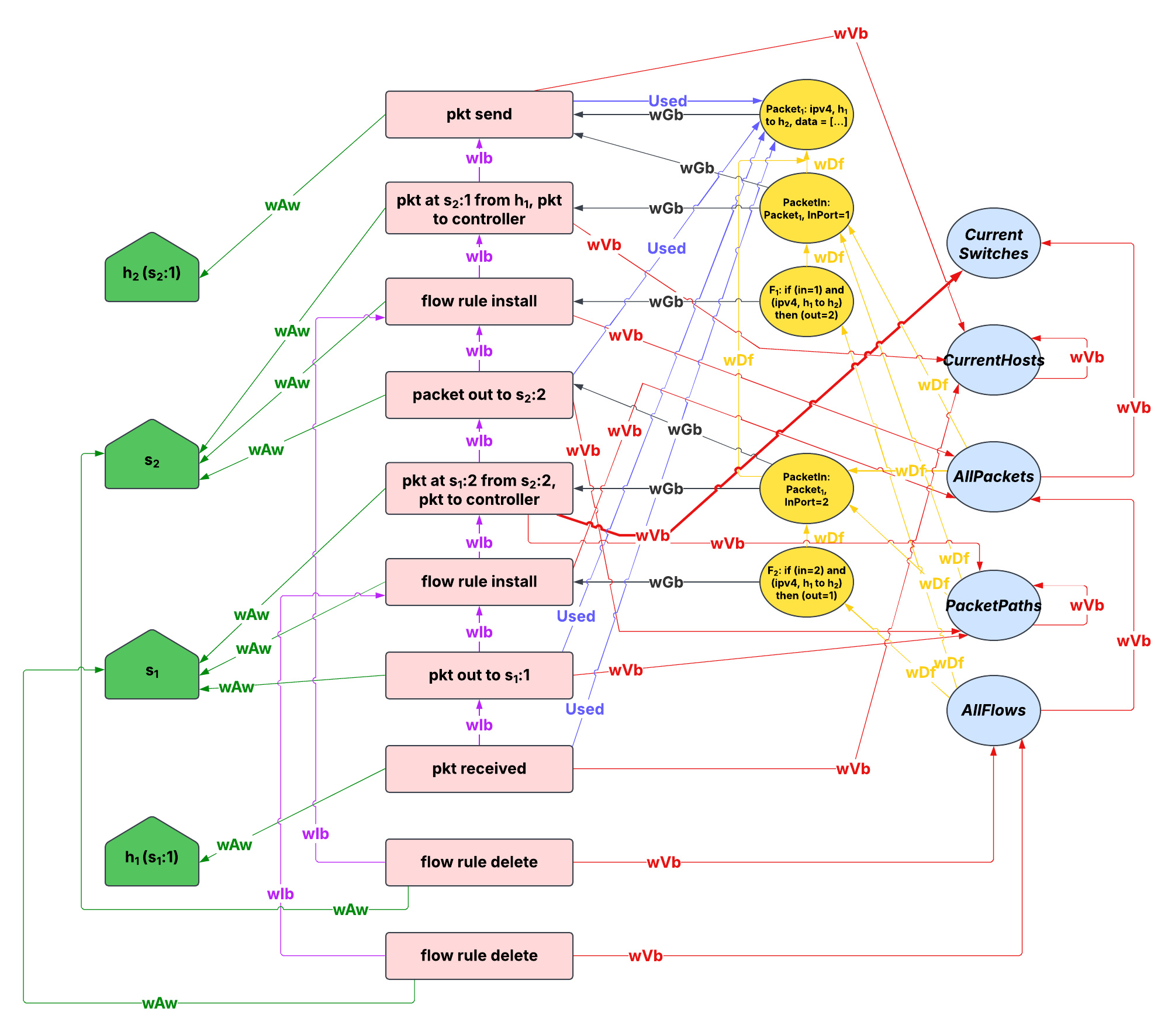
Security-aware Data Provenance for Multi-domain Software-defined Networks
This project proposes PRISM-Prov, a novel programmable, real-time, interoperable, security-aware, and multi-domain provenance framework to increase security, transparency, and overall trust in SDNs.
Malware Detection Engine
This project uses Machine Learning to predict whether a given executable is malicious using static (library imports, PE structure, etc.) and dynamic (API calls) features, forming the backbone of the detection engine.
View this project on GitHub↗

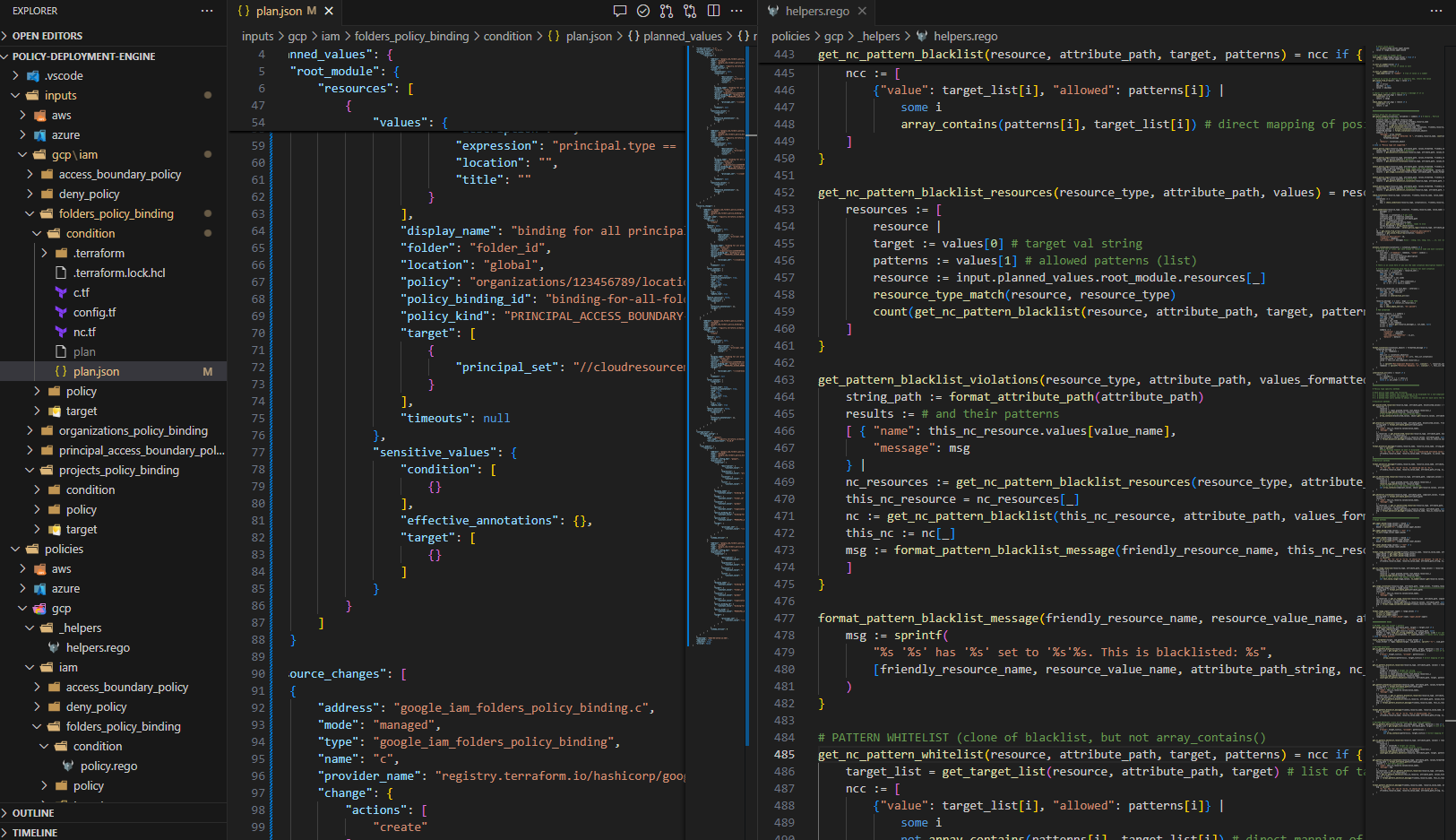
Policy Deployment Engine
Human error in cloud configurations has grave security implications. This group project aims to audit cloud resource infrastructure plans before deployment against a series of relevant security policies to ensure compliance and reduce risk.
View this project on GitHub↗
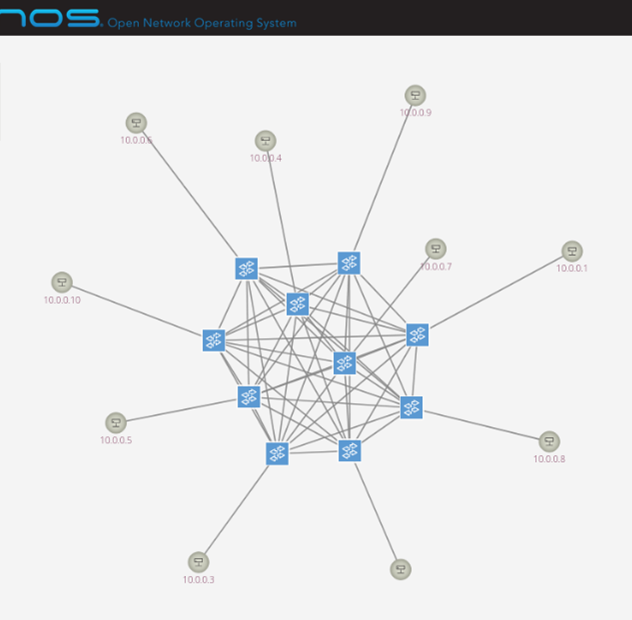
Peer-based DDoS Protection in SDNs
Denial-of-Service (DOS) attacks are the common cold of computer networking. This project explores how utilizing empty flow tables of neighboring switches help networks withstand such attacks longer.
View this project on GitHub↗

Low-and-slow DNS-based Covert Data Exfiltration
Data exfiltration is the art of siphoning data away from a system undetected. Threat actors prefer this as it allows for persistent access. Modern, highly-secure systems scrutinize all kinds of traffic, especially outbound ones, making the "escape" from a system difficult. This project explores how a malicious program could covertly exfiltrate data from a victim machine by encoding information in the form of subdomains within DNS queries, taking advantage of how prevalent and important the DNS protocol is in many computer systems.
View this project on GitHub↗

Fraudulent Credit Card Transaction Detector
This project uses Machine Learning to determine whether a transaction is fraudulent based on anonymized features.
View this project on GitHub↗
...and many more!
Apart from this curated selection, please click the button below to explore other projects that I've worked on.