Peer-based DDoS Protection in SDNs
SDN, DDoS, Network Security
This project is based off the work of Yuan et al. [1], and explores how empty flow tables of neighboring switches can be used to increase a network's holding time against DDoS attacks. Please refer to this report↗ for a more detailed writeup of the project.
Project Summary
Background
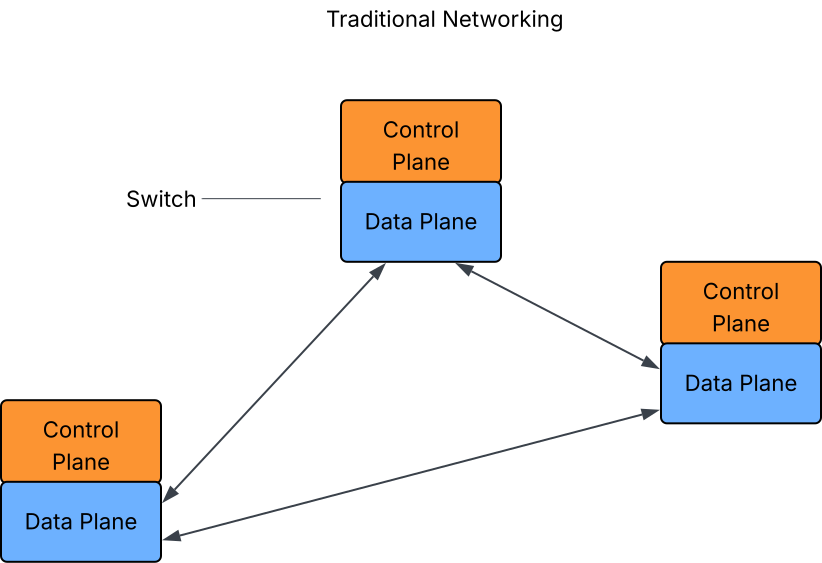
In computer networks, data is transmitted as packets across optimally-determined paths. Traditional networks manage both packet forwarding and path determination within the same hardware device, such as routers and switches, relying on various independent protocols (ARP, STP, OSPF, EIGRP, BGP, etc.) to achieve different functions. This tight coupling hinders scalability and flexibility. Software-defined Networks (SDNs) address these limitations by decoupling the data plane (packet forwarding) from the control plane (path decision-making).
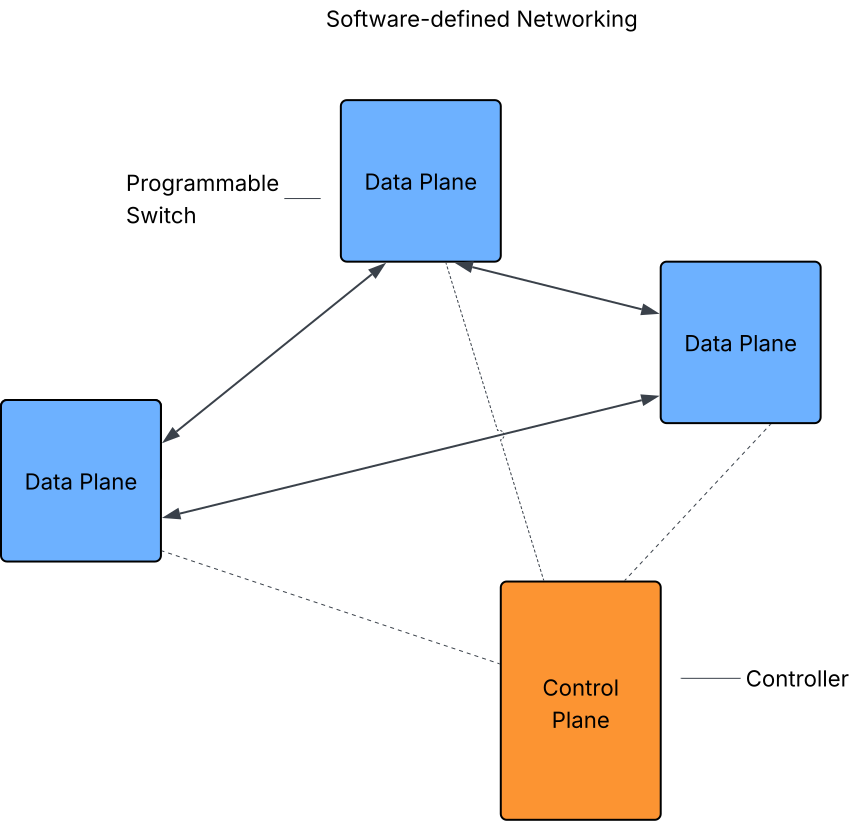
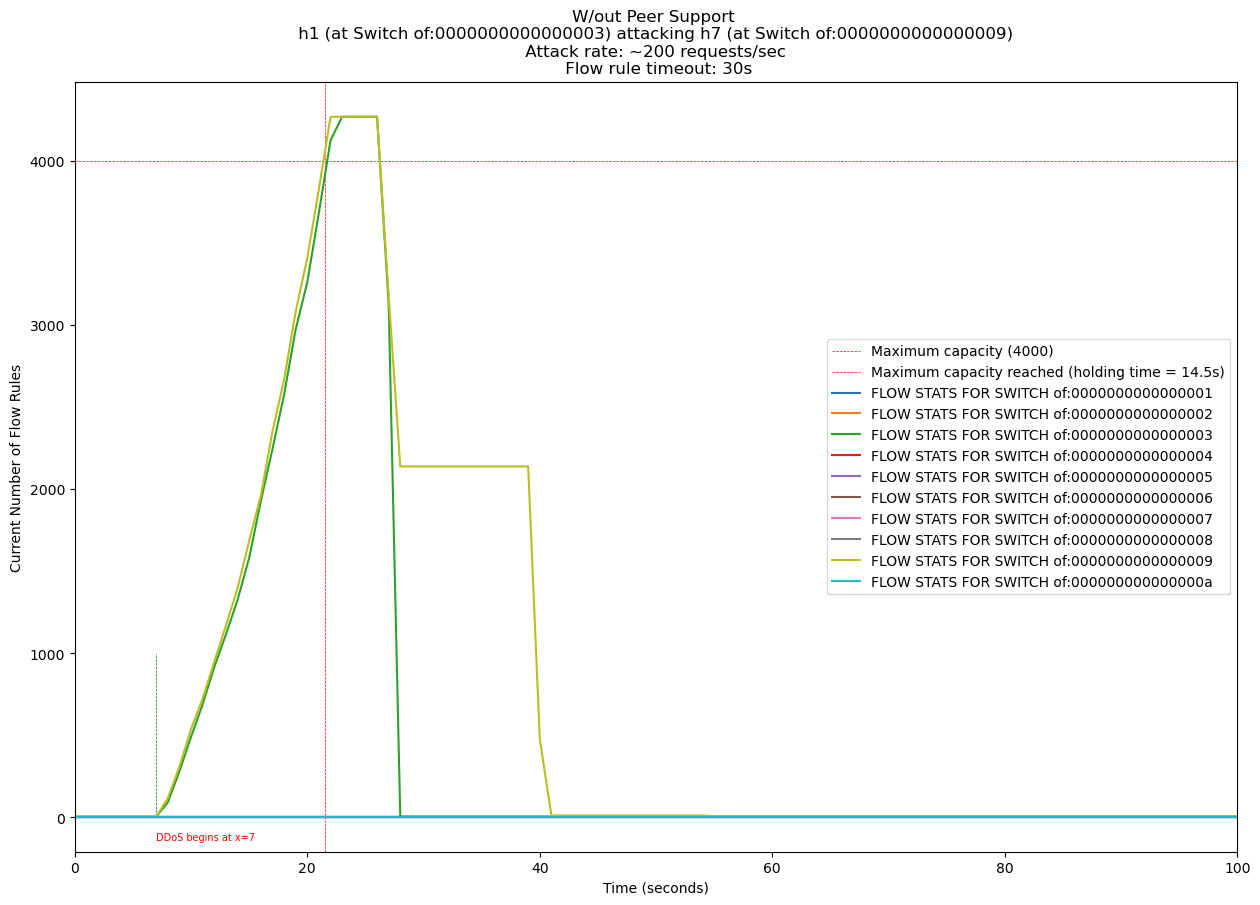
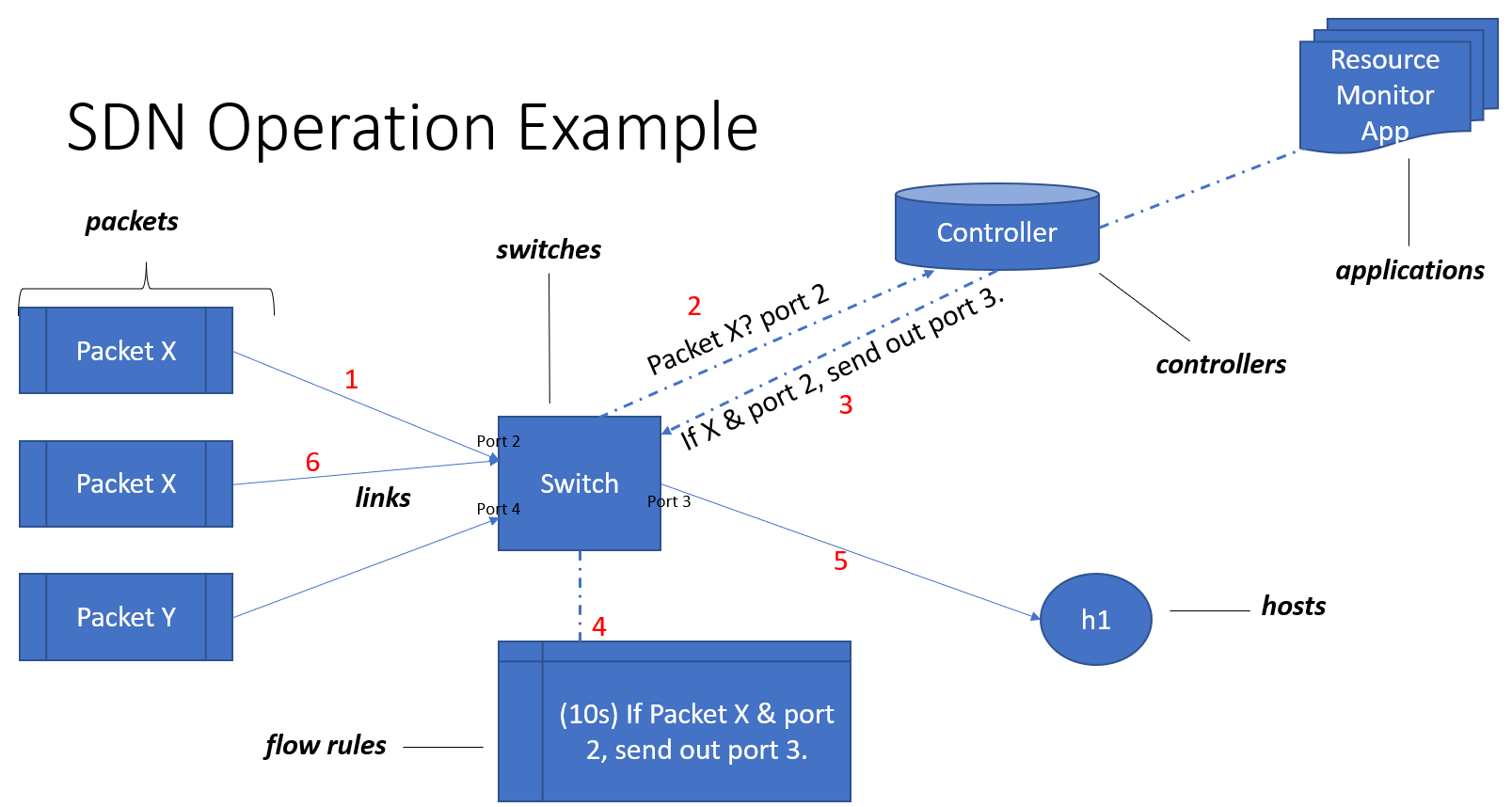
Figure 4 presents a typical SDN operation in a switch for an arriving packet. The controller installs in that switch a flow rule, which tells the switch what to do with that packet (based on extracted information). For example, if the packet arrived at port 2 from host h2, destined to host h1 (which is connected to the switch at port 3), a flow rule is installed to send it along that port. This rule has a lifetime, say 15 seconds. If within those 15 seconds a similar packet (same origin, destination) arrived, it is treated as per the active flow rule - the switch does not need to contact the controller anymore.
Switches in an SDN uses Ternary Content-Addressable Memory (TCAM) registers for fast lookups. However, TCAM entries are limited due to its high costs and power consumption, usually limited to around 8000. An attacker could exhaust this limit by sending spoofed packets, each with unique details, triggering the creation of more flow rules than available space, effectively stalling the switch.
Solution
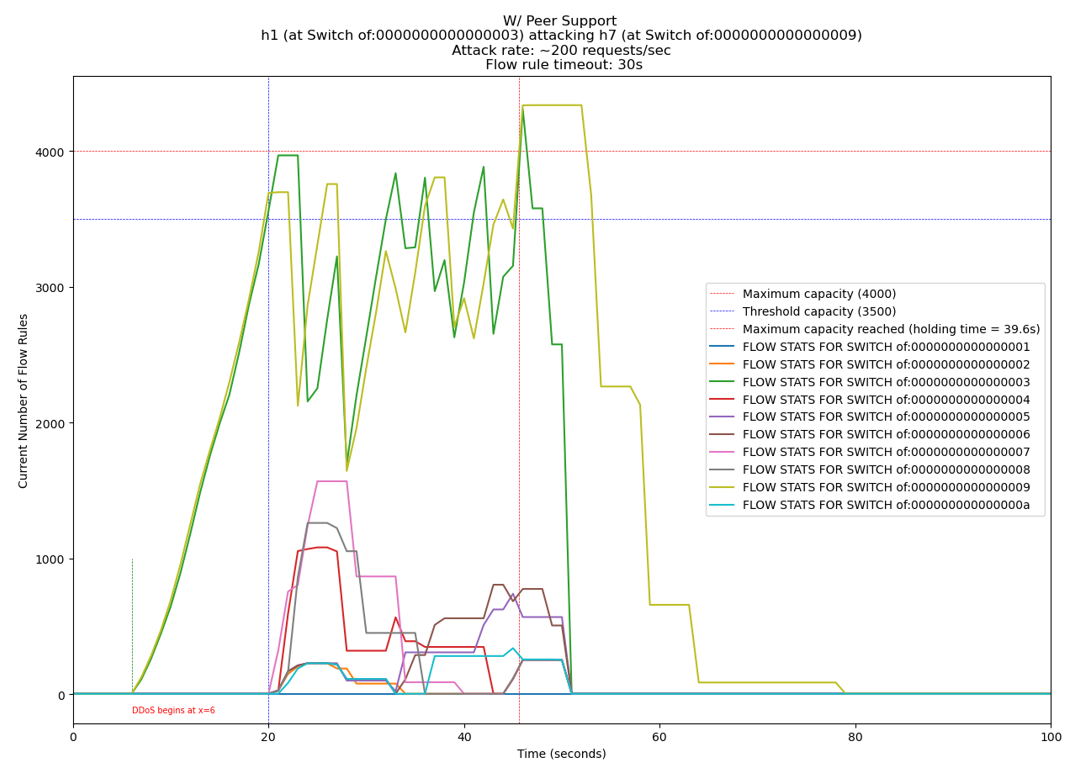
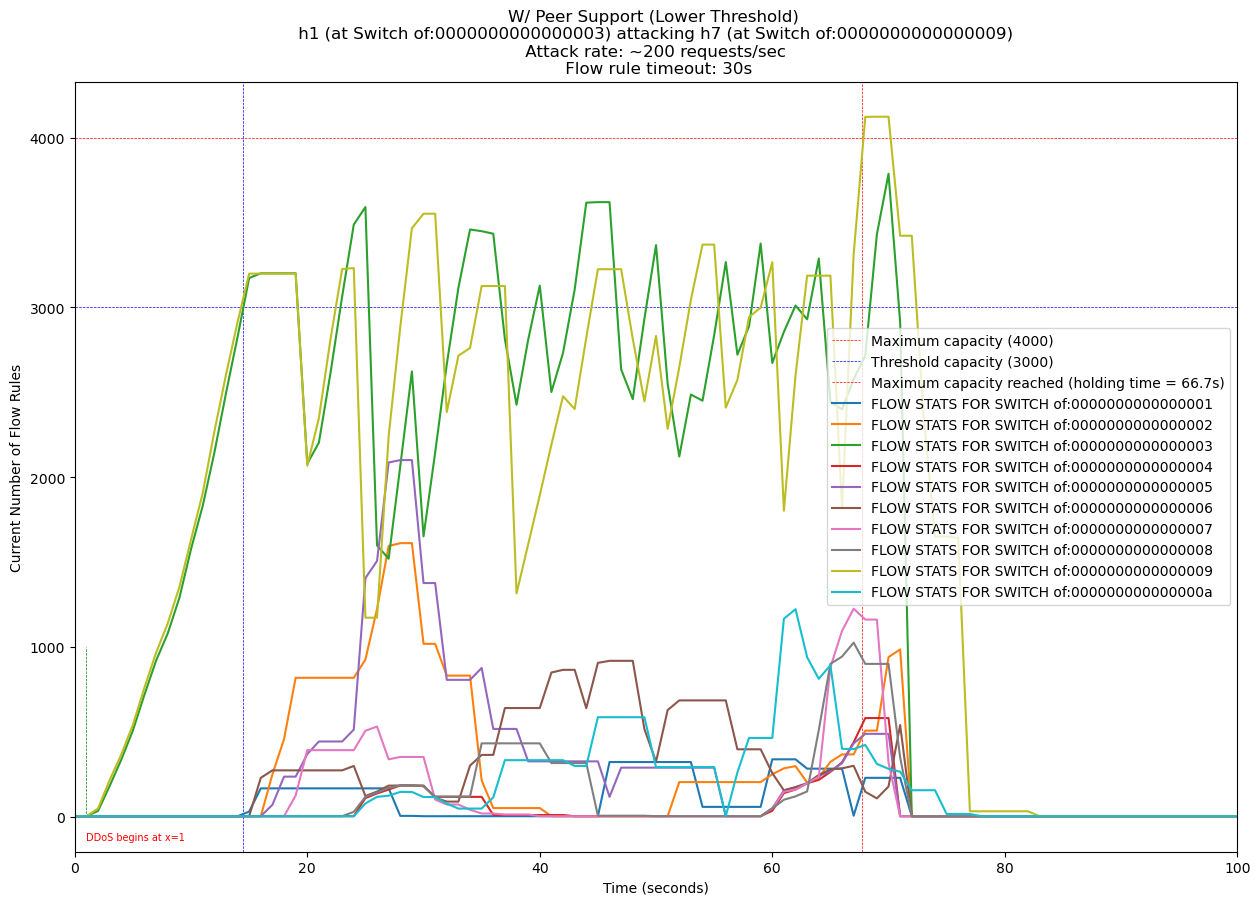
[1] showed how the empty tables of nearby switches can offload incoming traffic of a targeted switch, assuming, of course, an average attacker and that only a single switch is being targeted. For this to effectively work, the network should be mesh topology; i.e., every switch is connected directly to another. This project operates on the same principle, but the implementation is my own.
Firstly, we monitor the flow table of each switch. Two conditions should then be
satisfied:
1 - that the number of flows has exceeded a pre-defined limit,
2 - that the rate of inbound packets has exceeded a pre-defined limit.
Afterwards, we install a wildcard flow rule (i.e., for any new packet at all, do this ...) that directs traffic to a nearby peer switch with sufficient flow capacity should they too become inundated. The same is done for every switch. Default flow rules triggered like this have a natural lifetime. The number of switches in the network is directly proportional to how longer it can withhold an attack. Combined with the fact that each switch has a direct connection to every other, this method increases attack response times before the network can be stalled.
This method seems very primitive, as it is a mere (though successful) proof-of-concept. An attacker with normal resources will be exhausted using existing network power. Defense systems can always refine it further. See the following graphs tracking the holding time (defined as the time it takes for any one switch to have reached the maximum flow capacity) in a network with and without the method.